Information Security Assessment
Protect the confidentiality, integrity and availability of your organization's information.
A comprehensive review of the safeguards on your information
Protecting your sensitive information takes more than a good firewall and antivirus. It’s affected by everything your organization does: the policies your team members follow in the office, the ease of remote access to your server, the locks on your doors, even your organization’s social media presence.
If you can't measure it, you can't improve it
Often, many of these safeguards happen by chance or habit. After all, it’s common practice to lock the office door, report suspicious emails, and keep sensitive info out of plain sight. But if these defenses only happen by default, you have no way to rely on them, and malicious actors are skilled at finding overlooked vulnerabilities. When it comes to cybersecurity, passive defenses are no match for an active attack.


Maximize your security investments
Mytech’s Information Security Assessment is not an audit: it’s an opportunity to evaluate every aspect of your organization’s information security. Learn where your defenses are robust, and where they’re lacking…or even nonexistent. By investigating the nooks and crannies of your security alongside a trained Assessor, you’ll get a complete picture of where your organization stands…and how to maximize your security investments.
Measure Your Organization's Risk
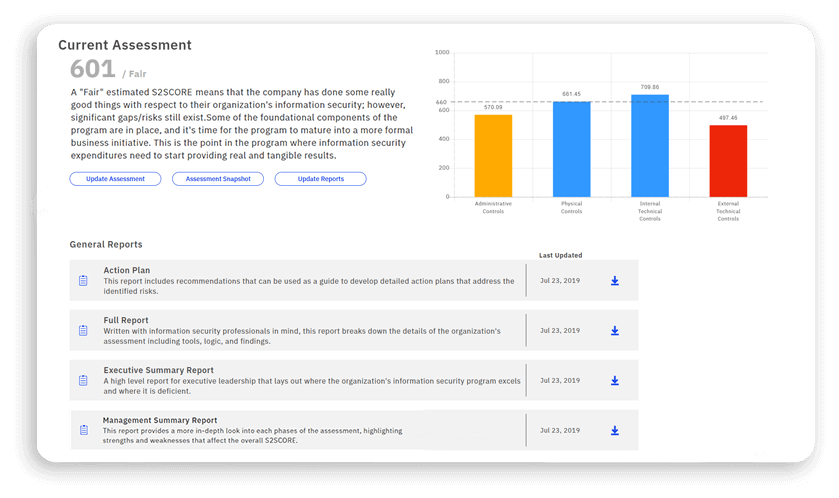
The Information Security Assessment examines three different areas of your organization’s security. While some of these security controls are obvious, others are often overlooked – which is why it’s so critical to review each type completely to find the gaps.
Administrative Controls
Policies, awareness training, guidelines, standards, and procedures
Technical Controls
Split into Internal & External designations
Internal – Firewalls, anti-virus software, and patch/software vulnerability
External – Search engine indexes, social media, DNS, and port/vulnerability scanning
By reviewing your protections in each of these key areas, you can get a clearer picture of the work you have to do to mitigate your specific risks – either to meet compliance standards such as HIPAA, PCI, or DFARS, inform your cybersecurity insurance decisions, or simply protect your organization’s critical information and infrastructure from outside influence.
The assessment involves a complete review, inspection, and evaluation of your organization’s different security controls, conducted by our trained Information Security Assessor. Working from an exhaustive list of questions, measurements, and standards, the assessor will take stock of your security controls and your level of risk in various areas.
This includes
Physical Office Visits
Document & Database Review
Team Member Interviews
Although you could, in theory, ask yourself many of these security questions, the value of an outside observer is undeniable. By explaining your controls and policies to our assessor, not only can you be certain of an objective assessment, you can also get the chance to articulate your actions and the intentions that motivated them. More than once, our clients have had “Aha!” moments about their own security, mid-explanation.
Build a comprehensive roadmap
Review Analysis
Plan & Prioritize
Mitigate Risks
In addition to your thorough information security analysis, you’ll also receive a plan of action for addressing those shortcomings, plus consultation from us on how to prioritize those actions.
Our managed services clients will benefit even more, thanks to integration with our strategic planning sessions and check-ins.
The Information Security Assessment is more than just a one-off tool: it’s a way to constantly build security habits to protect against the threats of today…and tomorrow, too.
The Information Security Assessment examines three different areas of your organization’s security. While some of these security controls are obvious, others are often overlooked – which is why it’s so critical to review each type completely to find the gaps.
Administrative Controls
Policies, awareness training, guidelines, standards, and procedures
Technical Controls
Split into Internal & External designations
Internal – Firewalls, anti-virus software, and patch/software vulnerability
External – Search engine indexes, social media, DNS, and port/vulnerability scanning
By reviewing your protections in each of these key areas, you can get a clearer picture of the work you have to do to mitigate your specific risks – either to meet compliance standards such as HIPAA, PCI, or DFARS, inform your cybersecurity insurance decisions, or simply protect your organization’s critical information and infrastructure from outside influence.
The assessment involves a complete review, inspection, and evaluation of your organization’s different security controls, conducted by our trained Information Security Assessor. Working from an exhaustive list of questions, measurements, and standards, the assessor will take stock of your security controls and your level of risk in various areas.
This includes
Physical Office Visits
Document & Database Review
Team Member Interviews
Although you could, in theory, ask yourself many of these security questions, the value of an outside observer is undeniable. By explaining your controls and policies to our assessor, not only can you be certain of an objective assessment, you can also get the chance to articulate your actions and the intentions that motivated them. More than once, our clients have had “Aha!” moments about their own security, mid-explanation.
Build a comprehensive roadmap
Review Analysis
Plan & Prioritize
Mitigate Risks
In addition to your thorough information security analysis, you’ll also receive a plan of action for addressing those shortcomings, plus consultation from us on how to prioritize those actions.

Our managed services clients will benefit even more, thanks to integration with our strategic planning sessions and check-ins.
The Information Security Assessment is more than just a one-off tool: it’s a way to constantly build security habits to protect against the threats of today…and tomorrow, too.
Get Started
Take an active role in your information defense
If you’re interested in a thorough review of your safeguards and preparedness, and ready to take an active role in your own digital defense, we’re ready to talk. Request an Information Security Assessment, or get answers to any questions you may have about the process.
